Azure
Self-hosted Setup Guide
This guide will help you and your team install LogRocket on cloud infrastructure you control. LogRocket deployments rely on a few tools, each of which is available on macOS, Windows, and Linux:
- Terraform v1.3.x for provisioning services required by LogRocket
- Helm 3.x for installing and upgrading LogRocket
- Kubernetes CLI for managing and inspecting the Kubernetes cluster. See download links in Kubernetes CLI section
Usage of these tools is described below. We recommend following the steps below in Git Bash on Windows.
Kubernetes CLI
The Kubernetes CLI, kubectl, is required by Terraform for several setup operations, and will be useful post-setup for managing and inspecting the Kubernetes cluster. Install kubectl links below.
# macOS
curl -LO "https://dl.k8s.io/release/v1.32.1/bin/darwin/amd64/kubectl"
# Windows
curl -LO "https://dl.k8s.io/release/v1.32.1/bin/windows/amd64/kubectl.exe"
# Linux
curl -LO https://dl.k8s.io/release/v1.32.1/bin/linux/amd64/kubectlTerraform
Configure
Authentication
Terraform supports authenticating to Azure through a Service Principal or the Azure CLI. Authenticating via the CLI is easiest. Doing so requires installing the Azure CLI and signing in.
IF you are using Azure Government, remember to run the command below to set az to AzureUSGovernment
az cloud set -n AzureUSGovernmentThen use the command below to login.
az loginMultiple Subscriptions
If you have multiple subscriptions in your account, you need to choose one to use with Terraform before you can apply any configuration. List subscriptions associated with the account:
az account listSet your chosen subscription using the id field corresponding to it:
az account set --subscription="00000000-0000-0000-0000-000000000000"Provision
Now you're ready to apply Terraform configuration. You'll download our Terraform configuration, fill in any relevant values, review the changes that will be applied, and finally apply it.
Our Terraform configuration is available for download and should be unzipped to its own folder:
wget https://storage.googleapis.com/logrocket-terraform/terraform-azure.zip
unzip terraform-azure.zip -d terraform-azure
cd terraform-azureInitialize Terraform to download dependencies:
terraform initUse the terraform.tfvars file in your selected directory to specify Terraform variable values. The defaults are fine in most cases. If you're using Git Bash on Windows, uncomment the local_exec_interpreter line.
After reviewing the contents of terraform.tfvars and making sure they're correct, do a Terraform dry run:
terraform planIf that looks correct, apply the configuration:
terraform applyYou will be prompted for approval before the configuration is applied. If something goes wrong, it's safe to re-run this step repeatedly. You can also re-run this step to modify existing, Terraform-managed infrastructure.
After applying, Terraform will output some values and files:
- The
terraform.tfstatefile is how Terraform remembers what it's managing. The state contains sensitive information. Keep this file. It can be committed to a private repo or stored remotely using a Terraform backend (e.g., Azure Storage). - The
postgres-connection-nameoutput is the required value forpostgres.hostin Helm values. - The
postgresql_passwordoutput is the required value forpostgres.passwordin Helm values. - The
storage_nameoutput is the required value forazure.storage.accountin Helm values. - The
storage_access_keyoutput is the required value forazure.storage.accessKeyin Helm values. - Use the
resource_group_nameoutput as the value of the--resource-groupoption when connecting to your new AKS cluster below.
These output values can be retrieved at any point by running terraform output.
Verify
You should now be able to access your new AKS cluster. To do so, install kubectl. Then connect it to your cluster by running:
az aks get-credentials --resource-group <resource_group_name> --name logrocketTo verify that you're connected and that the cluster was created correctly, check that worker nodes have joined your cluster:
kubectl get nodesYou should see a list of two or more nodes.
Postgres Database Extension
Once the terraform is complete, you will have a new Azure Database for PostgreSQL flexible server setup in the LogRocket resource from in Azure. LogRocket requires you add one additional extension to the database instance before installing LogRocket. In order to do this, please see instructions below.
- Log into https://portal.azure.com
- Navigate to the newly create LogRocket resource group
- Select the Azure Database for PostgreSQL flexible server in the resource group
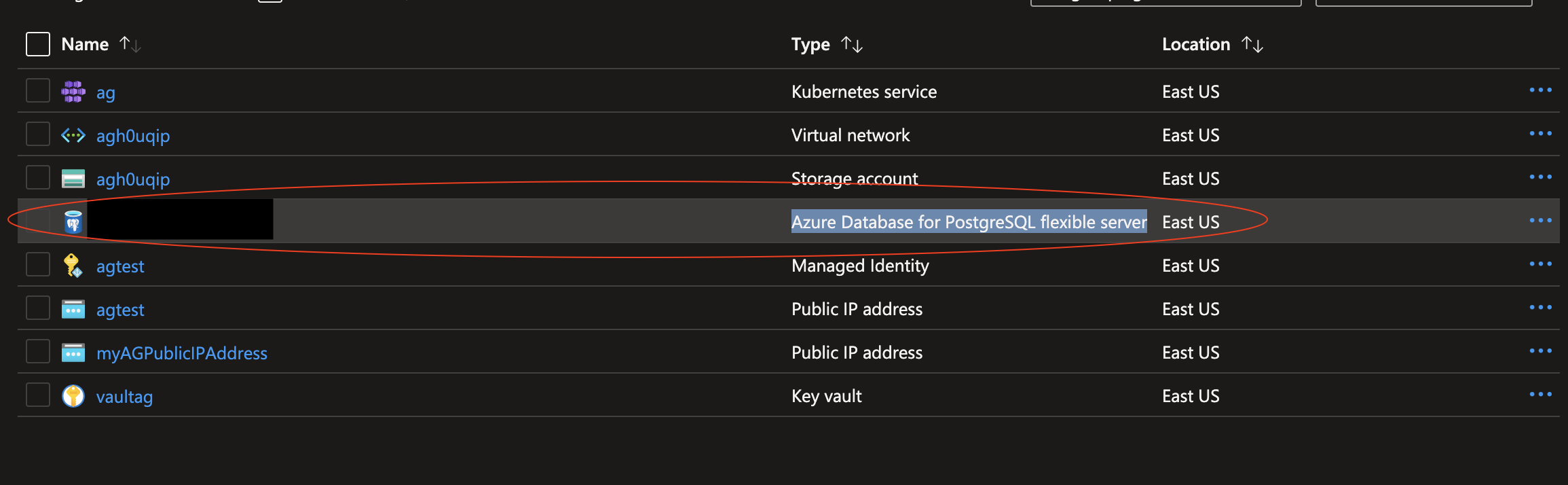
- Select Server Parameters in the left-side menu under Settings
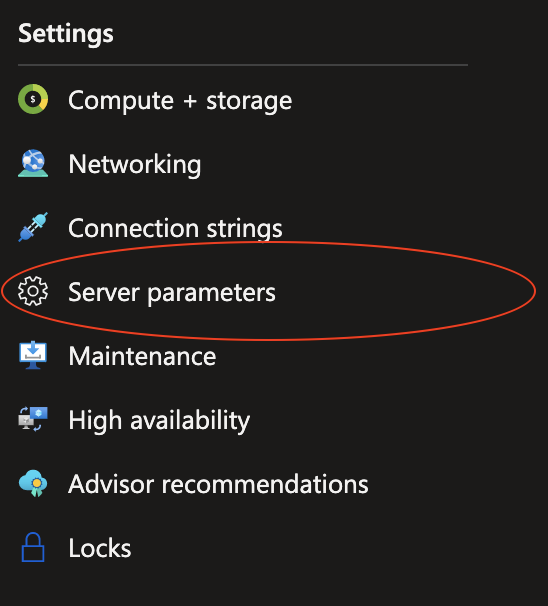
- In the search bar on in Server Parameters search for azure.extensions
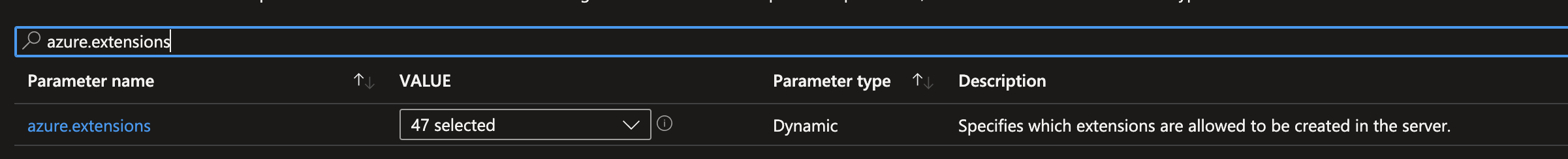
- Select the down arrow in the Value column and select the checkbox next to CITEXT

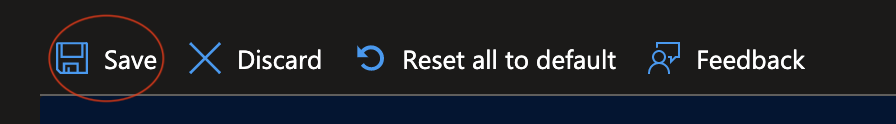
- Select the Save button.
Once this is complete, you can move onto the Helm section of the instructions.
Helm
Configure
Before installing the LogRocket Helm chart, you need to configure it. Ask the LogRocket team for your values.yaml configuration file. The file will instruct you to fill out a handful of values, each marked with a TODO comment. Most of these were output by Terraform above. You just need to copy and paste them.
The terraform outputs include sensitive data such as passwords. These outputs will have <sensitive> next to them. These values will be necessary and you will need to add them to your values.yaml file.
In order to retrieve the Terraform outputs to add to your values.yaml file, please navigate to the LogRocket Terraform directory/folder and run the command below to see all the values.
terraform output -json*IF you are using Azure Government, you will also need to set storage.endpointSuffix to core.usgovcloudapi.net. The storage block should look like below.
storage:
# TODO: name of the Azure storage account created by Terraform
account: ''
# TODO: an access key associated with the Azure storage account created by Terraform
accessKey: ''
endpointSuffix: core.usgovcloudapi.net*IF you are using Azure Government, you will also need to change pgbouncer.serverSSLmode to require. The pgbouncer block should then look like below.
pgbouncer:
replicas: 1
serverSSLmode: 'require'
azureFlexServer: true
Keep track of your values file!You'll need it to apply upgrades. The upgrade process is detailed below.
Deploy
After reviewing the contents of your values file and making sure they're correct, you're ready to install LogRocket.
Install LogRocket:
kubectl apply -f https://storage.googleapis.com/logrocket-charts/cert-manager/v1.18.3/crds.yamlhelm install --values values.yaml --wait --timeout 1500s logrocket oci://us-central1-docker.pkg.dev/logrocket-artifacts/helm3/logrocketMonitor the release deployment:
While LogRocket is installing, in a second tab or a new window of your shell, you can run the commands below to monitor LogRocket coming up. DO NOT running the commands in the same tab/windows that you are running the helm upgrade command:
kubectl get pods
kubectl get eventsIf the helm upgrade completed successfully, you have successfully installed LogRocket and can move on to the DNS section.
*IF the LogRocket upgrade did not complete successfully, you have the option to tear down the release and try the upgrade again. This is only recommended for initial installs of LogRocket. Please see PURGE and DELETE section at the bottom of the doc.
DNS
After deploying LogRocket, you must create a DNS A record pointing at the IP address of your cluster's load balancer. To get the IP address, run:
kubectl describe svc logrocket-nginx-ingress-controller | grep "LoadBalancer Ingress"Create an A record associated with this IP using your DNS provider of choice. You may have to wait several minutes for the DNS change to propagate and for the cluster to complete TLS setup.
Azure Blob Service
The initial LogRocket installation will create several Azure Blob Service containers for you. Follow these instructions to set up CORS for Azure Blob Service. You must allow your LogRocket dashboard (e.g., https://logrocket.example.com) to make OPTIONS, GET, and HEAD requests. Cache the preflight OPTIONS request for at least an hour. Your CORS rule should look something like this:

Follow these instructions to create a lifecyle policy for objects in the logrocket-messageblobs container. They should be deleted after 3 days.
Upgrade
To upgrade the LogRocket chart, simply repeat the installation step:
helm upgrade --values values.yaml --wait --timeout 1500s logrocket oci://us-central1-docker.pkg.dev/logrocket-artifacts/helm3/logrocketIntegrate
Login into your LogRocket dashboard to access the SDK installation instructions which will enable you to send data to your LogRocket instance.
Update License Key
- Open your values.yaml file
- Find the enterprise block. It should look similar to the below example.
enterprise:
# string consisting of lowercase letters, numbers, and/or hyphens (e.g., company-name)
singleOrgSlug: 'logrocket-example'
# license key provided to you by LogRocket
licenseKey: 'obhh5rscbxmzhvewhsipobhh5rscbxmzhvewhsipcsbvljsnvlksnvdfsbvlsbdvdsbkjnslnclsdnvsbnvlsnlvnslkvnsklnvslknvsnvkl;nks;nvlskvnslnvjslknvls'
multiTenant: false- Replace the licenseKey with your new license key provided by LogRocket
Option 1: Applying License Key to the Same Version of LogRocket (Recommended)IF you wish to apply the license key to the same version of LogRocket and do not wish to upgrade to a new version of LogRocket at the same time, follow the instructions below.
- Run the command below to see what current version of LogRocket you are running.
*You will see your current version of LogRocket where the STATUS column has status DEPLOYED
helm history logrocket- Make note of the version of LogRocket you are running. You can see the current version in APP VERSION column.
- Run the helm upgrade command below against your values.yaml file. Change {your version} in the command to the version of LogRocket you are currently running
helm upgrade --values values.yaml --wait --timeout 1500s logrocket oci://us-central1-docker.pkg.dev/logrocket-artifacts/helm3/logrocket --version {your version}
Option 2: Apply License Key and Upgrade LogRocket to Latest VersionIF you wish to apply your license key but also upgrade LogRocket to the latest version of the software, follow the instructions below.
- Run the standard helm upgrade command against your values.yaml file.
helm upgrade --values values.yaml --wait --timeout 1500s logrocket oci://us-central1-docker.pkg.dev/logrocket-artifacts/helm3/logrocketPURGE and DELETE
FOR NEW INSTALLS ONLYIf something goes wrong during the initial install, you may need to tear down the LogRocket release and attempt a fresh install. Please see the purge and delete commands below. Only use for initial installs OR after speaking to LogRocket Support first. If the install succeeded, you can move on to DNS
helm delete logrocket
kubectl delete jobs --all
helm upgrade --values values.yaml --wait --timeout 1500s logrocket oci://us-central1-docker.pkg.dev/logrocket-artifacts/helm3/logrocketUpdated about 1 month ago
